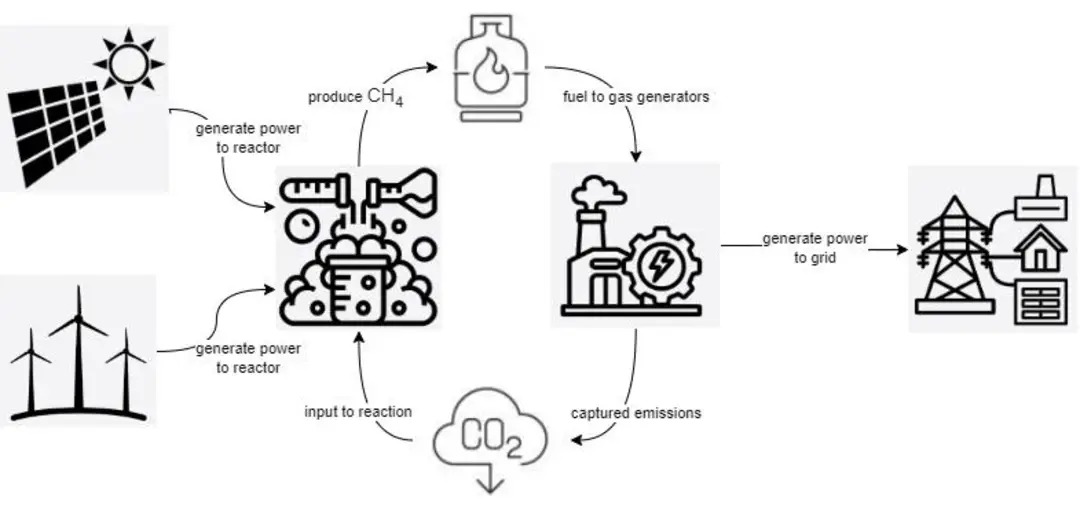
What is the metaverse?
Facebook’s renaming as Meta brought attention to the rise of the metaverse. I would like to explore how to think about the metaverse and related technologies.
the “metaverse” is a hypothetical iteration of the Internet as a single, universal, and immersive virtual world that is facilitated by the use of virtual reality (VR) and augmented reality (AR) headsets.
https://en.wikipedia.org/wiki/Metaverse
This description identifies VR and AR headsets as an essential feature. However, I believe headsets are extraneous. I contend that headsets are not worth pursuing for the general public. What is essential is the evolution to the next generation of the Internet to become a single, universal, and immersive virtual world.
Next Generation of the World Wide Web
Today’s most important Internet technologies are known as the World Wide Web (WWW). The next generation of the Internet would be the third. The first generation delivered mostly static hypertext content from content producers to consumers. Today’s second generation services and platforms enable users to create content and distribute that content to an audience.
Ethereum co-founder Gavin Wood coined the term “Web3” for the third generation. It envisions the WWW to be decentralized with blockchain technologies. Web3 would enable token-based economics.
I have a different perspective on Web3. To expand on this perspective, I wrote What do we want from Web3? In particular, I do not see Ethereum being a suitable basis for Web3. To fully realize the goals, Web3 will require additional innovations and decentralized technologies that are general-purpose and not vulnerable.
WEF interest in the metaverse
The metaverse has even attracted the attention of the World Economic Forum (WEF). They have published a document called Demystifying the Consumer Metaverse.
The World Economic Forum has assembled a global, multi-sector working group of over 150 experts to co-design and guide this initiative. The hope is that this will lead to cross-sector global cooperation and the creation of a human-first metaverse. The metaverse has the potential to be a game-changer, but it must be developed in a way that is inclusive, equitable and safe for everyone.
We can see from their own language that they intend to appoint their own people to co-opt the technology. They wish to set the direction for the technological innovations toward advancing their own agenda. That agenda seeks to design a better world, one in which liberty is curtailed, autonomy is surrendered, choices are restricted, and power is concentrated in anointed leaders.
Metaverse Agenda
Digital Identity
For the WWW to be more universal and immersive, a user should not have to login separately using distinct account credentials, when navigating to each site. The user should have a smooth and seamless experience. Digital identity is an essential element of continuity. A user can specify preferences and localization once, and have sites be personalized everywhere.
In today’s Web2, ad networks use crude techniques to attach an identity to users. IP addresses, tracking cookies, and browser fingerprinting are typical approaches.
Surveillance
Once users have a digital identity that is universally recognized, users can then be tracked. Ad tracking is a creepy annoyance. However, the most serious danger will be surveillance tied to authoritarian control.
The US government regulates economic activity by controlling the money and its flow through financial institutions and payment systems. Know Your Customer (KYC) and Anti-Money Laundering (AML) are policies for this control. Currently, such policies rely on verifying a person’s identity using some form of state issued ID, such as a driver’s license or passport.
We can expect the government to seize the opportunity to co-opt digital identity in Web3. A state-issued digital identity would provide a key element for the government to exert authoritarian control. This topic will be addressed later in this article, once we explore other requisite elements.
Digital identity would lead to the loss of anonymity in transactions. KYC and AML policies apply to financial transactions, but every type of transaction (i.e., any online action taken by the user) could be subject to surveillance. Surveillance of consumer behavior has commercial value to corporations. However, the unholy collusion between government and corporations is a hazard for individual rights, as we will expand on below.
Self-sovereignty
Similar to the need for crypto-currency holders to maintain self-custody of their private keys, a person’s digital identity should be protected similarly. This is known as Self-sovereign identity. The owner must be able to control the revocation and re-issuance of their own digital identity. This may be necessary to counter targeted harassment and cancel culture.
More generally, self-sovereign data refers to users maintaining custody and ownership over their own data. Without self-sovereign data, fourth amendment rights against unreasonable search and seizure have been eroded. Law enforcement requests to communications service providers for customer data have been allowed without warrants. Courts have ruled that customers have no reasonable expectation of privacy for records about them kept by service providers. We recover these rights by reorganizing services and Web3 to become decentralized and by allowing customers to take custody over their data.
Moreover, if users can take custody over their own services through self-hosting, they would gain sovereignty over the applications that implement functions against their data. The combination of self-sovereign identity, self-sovereign data, and self-sovereign services protects against deplatforming and third party policy abuse.
Physical Asset Tokenization
A digital representation of a physical object is termed a digital twin. Applications in the metaverse will rely on digital twins to accomplish many things, such as enabling physical objects to be explored and manipulated virtually in ways that are impractical in the real world.
Physical assets will need to be tokenized to identify them. Web3 includes the Non-Fungible Token (NFT). A NFT is a digital identifier denoting authenticity or ownership.
Once assets have digital identity, it becomes easier to track them for the purpose of monetizing them. One way is to attach digital services to those physical assets. Subscribing for support, maintenance, and warranty repairs is an example of a service that can be monetized online for physical assets.
The Internet of Things (IoT) goes further by connecting physical assets to the Internet. This enables digital services to make use of or add value to those physical assets. Sensors, cameras, and control systems come to mind as obvious use cases. However, everything imaginable could be enhanced with connectivity to digital services.
Intellectual Property Rights
Physical asset tokenization leads to the erosion of ownership. Intellectual property rights, such as those attached to embedded software components, are retained by the manufacturer. The consumer is granted only a license to use with limited rights. The consumer has no right to copy that software to other hardware. This protects the software vendor from loss of revenue.
Does the consumer have a right to sell the physical asset to transfer ownership? One would expect that the hardware and its embedded software are considered to be an integrated whole or bundle. Hopefully, the software license is consistent with that.
A digital service connected to the physical asset is remote and distinct. A boundary clearly separates that remote software from the physical asset. There is no presumption of integration. The terms of service would need to be consulted.
Modern software is maintained with bug fixes and enhancements over time. Increasingly common, the vendor charges the consumer a subscription fee for maintenance and support. Does the consumer have the right to continue using the asset without subscribing? Can ownership of the asset be transferred along with its software subscription?
These questions go to the erosion of ownership. Physical things, such as vehicles and farm equipment, are becoming useless hulks without subscriptions to connected digital services and software maintenance. Instead of owning assets, people are subscribing to a license to use. It’s like renting or leasing. According to the WEF’s Agenda 2030, you will own nothing, and you’ll be happy.
Right to Repair
Software capabilities are essential to the functioning of equipment and devices. The traditional ownership model of farm equipment, vehicles (i.e., cars and trucks), and mobile phones, is evolving to a model where the end user has a license to use. License terms may restrict the user’s rights to modify, maintain, and transfer that asset.
Traditionally, an owner of an asset expects to be able to repair, modify, or build upon the asset. He can do it himself, or he can contract work out to others. Manufacturers are eroding these rights. They don’t want their software to be tampered with.
Many legislatures are passing Right To Repair acts to preserve some semblance of ownership control over physical assets. However, remote connectivity to digital services may never be brought into the fold.
The World is Virtual and Physical
The relationship between physical assets and digital services, including the metaverse, is fraught. We should think of the metaverse as the landscape in which all future digital services reside. Increasingly, physical assets are connected inextricably to digital services. Thus, the physical world and the metaverse become tied.
Programmable Currency
Monetization of digital services will be integral to the metaverse. Crypto-currency will be a key technology in Web3 to enable the digital economy. As novel cryptos gain consumer acceptance, you can be certain that governments will take notice.
Government has an interest in controlling money. Fiat money is manipulated by the central bank and their monetary policy. The supply is increased by making loans, which is a means of counterfeiting money. Money-printing dilutes the purchasing power resulting in inflation. The biggest loans are to finance government deficit spending.
Government seeks to gain control by making money programmable. Central Bank Digital Currency (CBDC) is programmable fiat money for this purpose. Control includes regulating who may spend money, when, where, on what, and how much. Authoritarian control will be total.
- Who – digital identity
- When and where – surveillance over services
- What – physical asset tokenization
- How much – programmable currency
Authoritarian Control
The Chinese Communist Party (CCP) has implemented a social credit system of authoritarian control. Individuals are assigned a social credit score based on surveillance of their behaviors. Privileges, travel authorization, and access to services may be restricted based on social credit score.
Programmable digital currency will be the perfect tool for authoritarian regimes to control public behavior. With hard cash replaced, no economic activity would escape government surveillance and control. Discrimination and cancel culture will be institutionalized.
Alternative Reality
Instead of the dystopian future that would follow from a metaverse based on flawed Web3 platforms, we must proceed with caution. Every technology must be scrutinized for vulnerabilities to capture and corruption by centralized powers. Decentralization and self-sovereignty must be paramount.
Avoid crypto-currencies that are not Bitcoin. Shitcoins are all scams. They are all corruptible, already corrupted, or corrupt by design. This is especially true of CBDC (or any crypto that is a candidate).
Disregard the hype. Headsets will never gain broad adoption. People will not tolerate being detached from reality for extended periods. Immersive experiences are valuable. However, people need to be able to multitask. Visiting places in the metaverse must be possible while still remaining engaged with normal activities of daily life and work.
Protect your identity and data. Self-sovereign identity and self-sovereign data are essential. True decentralization is essential. Any Web3 platform that does not honor these principles should be rejected.
The future will be bright, if we refuse to accept technologies that leave us vulnerable. It is early enough in the development of Web3 and the metaverse to reject poor technology choices. As consumers are better informed, they can have an enormous influence on what technologies are developed and adopted. Ethereum’s first mover advantage in Web3 and Meta’s first mover advantage in metaverse should be seen as consequential as MySpace and Friendster were to Web2.